Using concolic execution for static analysis of malware

Reverse engineering is about reducing the complex equation of binary code into na abstract understandable form . Dynamic and static analysis can speed up the process to a large extent , but they have their limitations when malware further tries to obfuscate and add an extra layer of protection to make analysis harder . Hiding import calls , obfuscated strings , use of visualized code are some of the techniques which hinder static analysis ,even when binary is finally stripped to its original form . These entities are dynamically retrieved by a malware sample
Often times writing scripts is further required to recover hidden entities ( imports, strings , opcodes etc.)
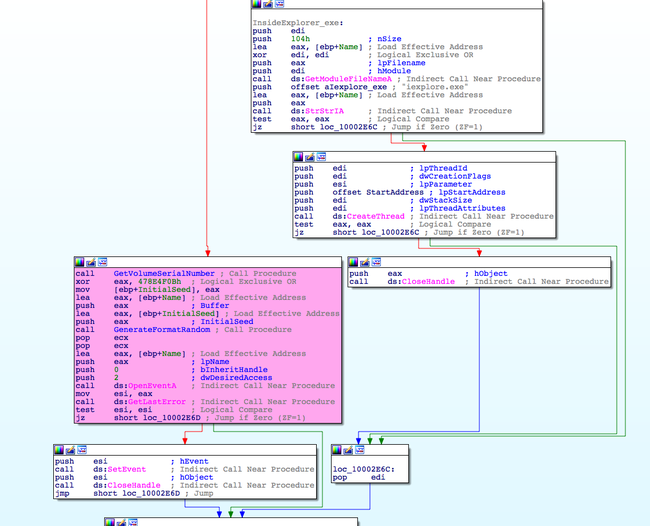
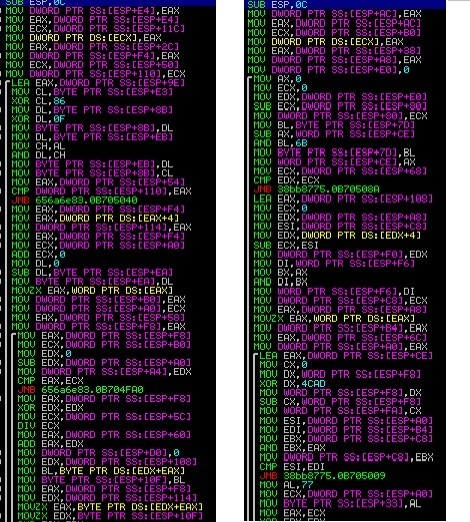
Below is an example of Tofsee spam bot , which features string obfuscation . Strings in this trojan are dynamically generated using a simple algorithm which extracts them from an encoded data buffer .

An easier...


















 ]
]