Notes On Vawtrak Banking Malware
Use of Heavens Gate technique for switching between 32bit and 64bit
Packed file is compressed and encrypted using several layers , discussing that would be irreverent here . At one point of time the a DLL is extracted which is actually installed and registered in an infected machine .
DLL happens to be a Component Object Model (COM) Binary DLL.
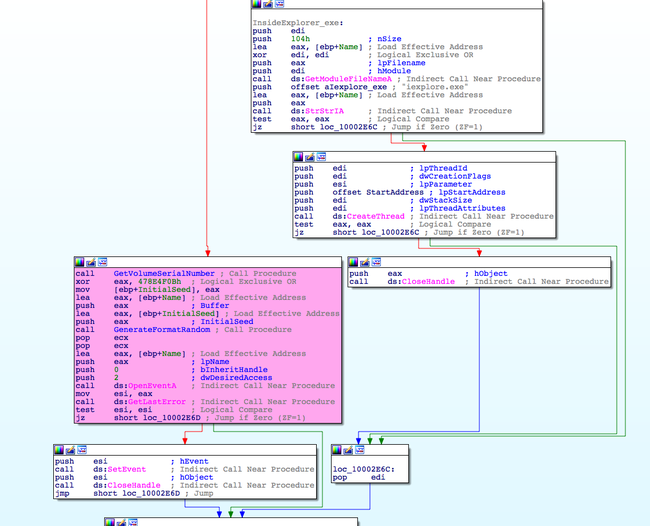
Entry point of the module is used for initialisation and sets some Named Events for checking an already running instance.
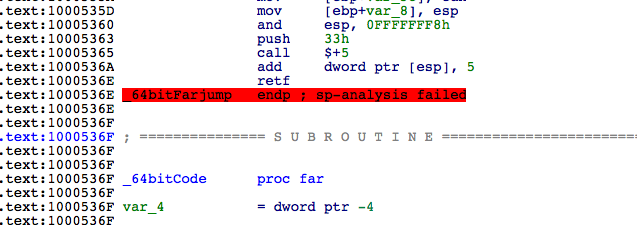
One important feature of Vawtrak is the use of Heavens gate for making 64bit calls though 32bit code . Basically in this technique , we make a far jump/call to segment 33h to land in 64bit environment under wow64 and segment 23h to come back to 32bit as mentioned here : http://vxheaven.org/lib/vrg02.html
As Vawtrak DLL comes in form of a 32bit PE file only . It makes heavy use of heavens gate to implement code injection in a 64bit process through its 32bit code .
It makes use of a publicly available library W64oWoW64 to make such calls
https://github.com/georgenicolaou/W64oWoW64
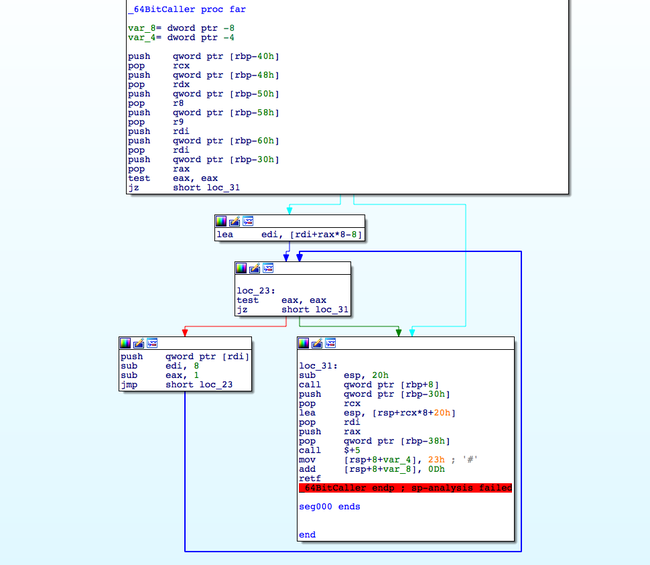
64 bit code pushes necessary arguments on to the stack and calls the 64bit function specified . Later execution is resumed back from 32bit code using 23h segment jump .
64Bit Loader code
Classical UAC bypass ( Deception )
Rather than using any known exploit for privilege escalation ( like the recent case of upatre downloader ) it uses an easy and effective way in doing so.
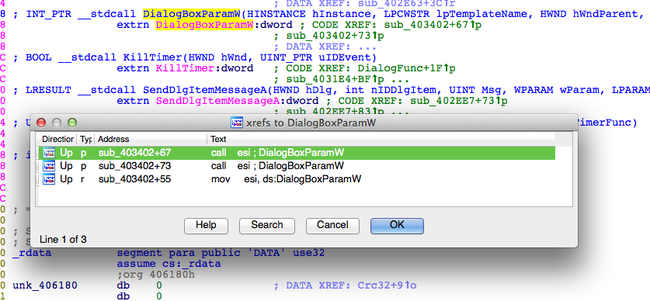
Looking at the resource entry table , we find two dialog boxes included within.
Looking at the cross references to the Dialog based function , we exactly match two of them .
It gets a default language preference and compares hardcoded defined values , currently only two of them are supported and is targeting english and german users
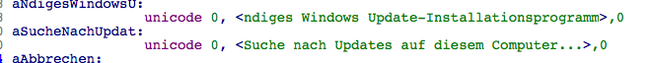
It creates two dialogs , which are faked as if updates are being installed on pc with a messages saying “Installing Update for Windows (KB2863058) (update 1 of 1)”.
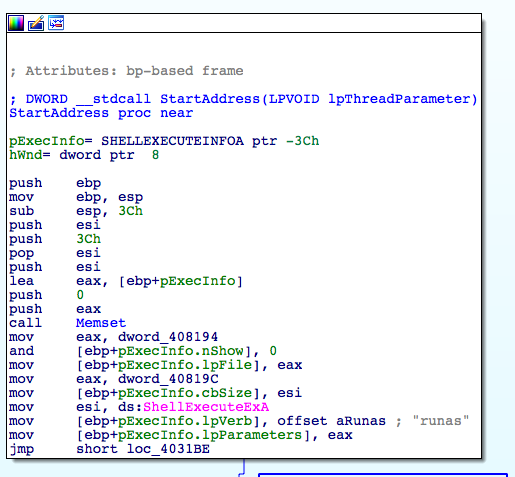
It executes a “ run as “ dialog in-order to run payload under administrator privileges